Last Updated on March 17, 2024 by Umer Malik
The more people use the internet in their everyday lives, the more vulnerable their data becomes. Over the past decade, data security has become one of the primary concerns for organizations, software providers, and ordinary people.
In their recent Cost of a Data Breach Report, IBM revealed that the cost of data breaches reached $4.24 million in 2021, which is an absolute record. According to IBM, data breach costs increased dramatically because of remote work caused by COVID-19. Along with that, IBM reports that compromised credentials were the reason for most breaches in 2021.
Experience has shown that cybercrime has not spared tech giants like Yahoo, Facebook, Apollo, and Twitter. This is the dark side of digitalization, which we are all adopting more each year.
In September 2020, the New York-based sports club owner Town Sports exposed sensitive data of 600,000 employees and clients due to storing data in an unprotected database and improper database security monitoring. The data revealed included full names, billing histories, phone numbers, emails, and mailing addresses. The timing of this massive data exposure was particularly unfavorable for the company, as due to COVID-19 they had to shut down 185 gyms and let almost all of their employees go. In the end, Town Sports filed for chapter 11 bankruptcy with $500 million in liabilities. In short, businesses should take adopting effective data protection strategies seriously. We’ll share some basic knowledge of effective data protection and professional data security technologies in this data security guide.
Table of Contents
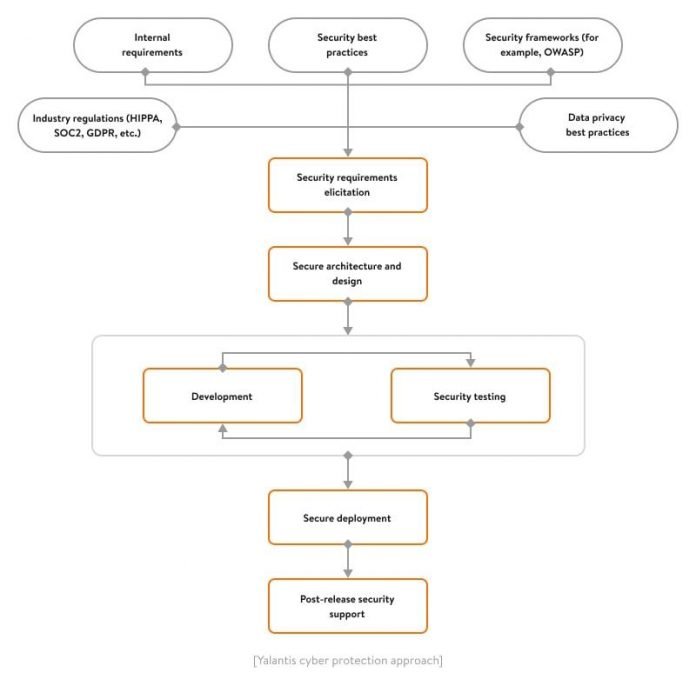
What makes a strong cyber security strategy?
Luckily, as the number of data breaches grows, more assets appear to prevent them.
A good cyber security strategy involves effective measures and controls implemented at each stage of the development process, from eliciting security requirements and developing a secure architecture to secure deployment and post-release support.
Approaches and technologies to ensure top-notch data security
Organizations invest in developing security assessment tools and training staff on cyber security measures. Gartner predicts that 40% of boards of directors will hire experts to form dedicated cybersecurity committees by 2025. In any case, the best way to secure your software from online threats today is to carefully follow basic techniques to prevent security vulnerabilities. We’d like to help you protect your data by explaining these basics.
Although the full list of cyber security measures you can take is far more diverse, we’ll focus on four components of ensuring data security:
- A risk assessment is an initial and fundamental step a company needs to take to ensure a holistic approach to cyber security. Estimating risks related to data exchanges and conducting threat modeling — the essential components of a security analysis — will help you define and prevent system vulnerabilities in your software architecture.
- HTTPS (HyperText Transfer Protocol Secure) is a more secure alternative to HTTP. A website with HTTPS protects users’ sensitive data much better than a website without it. Using this protocol is especially important for sites that accept payments or require users to enter confidential information.
- End-to-end encryption ensures the privacy of communication between users. It’s a data protection method that encodes data to prevent data leaks during communication between a sender and recipient (e.g. when sending private messages or exchanging emails).
- NaCl (read as “salt”) is a fast and easy-to-use software library tailored to network communication, encryption, decryption, and signatures.
Let’s discuss each of these components in detail.
How can you assess cyber security risks?
A common practice is sticking to the OWASP Risk Rating Methodology as a tool for evaluating the likelihood and impact of a web application vulnerability.
The OWASP methodology is helpful when it comes to assessing how severe potential cyber security risks are in order to make informed decisions about actions to take in response. It represents a risk ranking and helps you save time and focus on understanding the most critical risks.
The risk rating system developed by OWASP will properly assess all the risks your company faces. However, each business’s vulnerabilities are unique. Therefore, the basic framework needs to be customized to fit each business case. The image below shows how you can do that.
After performing a risk assessment, you may find out, for example, that you need an HTTPS inspection. Then, you’ll need to ensure your HTTPS inspection products provide appropriate Transport Layer Security (TLS) certificate validation. Products that don’t provide secure TLS communications and don’t transmit error messages to the user are likely to compromise the end-to-end protections that HTTPS is designed to ensure.
Why serve a website via HTTPS?
HTTPS is also called HTTP over TLS or HTTP over SSL. Sites that are served via HTTPS have redirects, meaning that even if a user enters http:// in the address bar, they will automatically be redirected to a secure, encrypted https:// connection. The Transmission Control Protocol (TCP) helps HTTPS forward and receive data packets. This happens via port 443 using a TLS-encrypted connection.
HTTPS is based on so-called public-private key cryptography. The public key is used for encryption, while the private key is required for decryption. The private key is always secret. Both keys are randomly generated and stored on your server.
A Certificate Authority, or CA, signs digital certificates with a cryptographic key. All browsers have a list of trusted CAs. Once a certificate is signed by the CA, it’s marked with a green padlock in the browser’s address bar. This means the certificate is trusted and belongs to the domain. Services like Let’s Encrypt have made obtaining SSL certificates free.
How TLS/SSL helps the HTTPS protocol and connected components protect data
As a rule, a man-in-the-middle (MITM) attack intercepts HTTP session cookies to steal a user’s authenticated session and allow a hacker to act like the authenticated user. Encryption methods like Wi-Fi Protected Access (WPA) and other local IT solutions can complicate such an attack and protect your users’ critical data. However, if a site doesn’t require end-to-end HTTPS, an MITM attack still might be successful.
TLS/SSL helps the HTTPS protocol ensure cloud security and protect data when transmitting it online. When the protocol is used appropriately, data received by the client is encrypted, which means no third party can read it. You can also use TLS/SSL to securely connect components such as microservices with a database or load balancer.
If a mobile app is not using SSL, it connects, authenticates, and transmits information via the network in the form of cleartext. If proper application security isn’t enabled, it’s possible for an MITM attack to capture this information. Additionally, if an app uses SSL but doesn’t correctly verify the certificate, it starts to be susceptible to a man-in-the-middle SSL attack.
Is HTTPS enough to protect your app data?
As HTTPS becomes increasingly common, it begs the question: Why do you still need to encrypt your data end to end if HTTPS provides a high level of protection? HTTPS is essential, but it’s still just a piece of the cryptography puzzle. To find out what other security requirements your company needs, perform a self-check:
- Count how many times data gets decrypted and re-encrypted while traveling from a user to your system.
- Determine the number of systems that can access cleartext during transmission.
- Review the number of departments in charge of the data journey.
Now the limitations of HTTPS and the benefits end-to-end encryption provides should be clear.
What are the limitations of HTTPS?
It seems like with HTTPS data gets encrypted. But it’s not that simple. Encryption doesn’t happen at rest, which harms the data security ecosystem on both sides of the transmission process.
Additionally, HTTPS absolutely ignores everything that happens to data once the connection is terminated, even without your acknowledging it happened. For example, termination may happen at your load balancer.
This creates a vulnerability to attacks at practically any point of data processing (application, load balancer, server), both storage locations (mobile device, server), and the point of transmission (internal traffic).
The situation gets worse provided your server is the endpoint of your web API but the services used for processing, analyzing, sharing, and backing up data are located in different places. In this case, you can still use HTTPS, but you will never be sure if the data is encrypted. This means your data remains unprotected.
So how can we further secure communication between users?
End-to-end encryption best practices
So far, end-to-end encryption is considered the most secure way to exchange data online. This data protection technology allows for encrypting messages on both the sender’s side and the recipient’s side. Such an approach prevents third parties (hackers, governments, service providers) from accessing private information. So when end-to-end encryption is applied, the sender and the recipient are the only ones who have the private key that is needed to decrypt messages.
For email services, online chats, and a number of other systems we use in day-to-day life, encrypted messages may still pass through a company’s servers, where they’re decrypted and stored before being delivered to the recipient. This poses a real risk of users’ private information being read or misused if a service provider’s server is poorly protected.
End-to-end encryption is considered safer, as it involves only the essential parties in the data encryption process. With end-to-end encryption, a server from a service provider only passes messages, while the actual encryption and decryption happens on users’ devices.
How does end-to-end encryption work?
Asymmetric encryption is a modern implementation of end-to-end encryption. This encryption type uses a pair of keys (large numerical values) to make secure communication possible:
- A public key is used to encrypt data transferred between a sender and a recipient. This key is usually generated by a service provider and is available through a public directory to anyone who’s sending encrypted messages.
- A private key is used for decrypting the contents of a message encrypted with the public key. Along with that, only the recipient that has the private key can unlock the message.
Let’s say you want to text your friend Nicole and ask “What’s up?” in private using a secure end-to-end encrypted messenger. To do so, you’ll need Nicole’s public key to encrypt your message and turn it into so-called ciphertext.
Once your message is encrypted, you will send it over the public internet. On its way, your message can pass through a variety of servers. Still, the messenger service itself won’t be able to turn your ciphertext into plaintext to read it. Only Nicole with her private key can do so.
Key generation process for end-to-end encryption
With end-to-end encryption, there are no general or app-wide keys or certificates. Key generation and propagation across all chat members (participants) happens in the following way:
Another look at the use of end-to-end encryption: non-messaging use cases
End-to-end encryption makes sense whenever a two-way communication process includes exchanging sensitive data. Use cases include direct messaging, email communication, remote desktop access, and online banking.
Let’s explore the example of payment gateways. How can you protect credit card information? When a user enters payment information during checkout, this data is instantly encrypted and stays encrypted until it reaches the payment processor or acquirer, where it gets decrypted.
Implementing end-to-end encryption doesn’t necessarily require you to have expensive equipment or training — or to hire many technical specialists.
Keep in mind that reputable payment systems like PayPal encrypt card information themselves. Also, PayPal tracks all transactions around the clock to avoid fraud, email phishing, and identity theft. Retailers can’t access card information when they’re using PayPal’s Vault API, as each transaction is encrypted. The Vault API securely stores users’ card data so a retailer doesn’t need to keep that data on their servers.
Given that the main condition for secure communication using encryption algorithms is that no third party can access the encryption keys, exchanging keys is still a challenge. Ensuring a high level of digital privacy is possible using the Diffie-Hellman algorithm. Let’s see what it is and how it works.
How the Diffie-Hellman algorithm helps ensure secure key exchanges
The Diffie-Hellman algorithm is known as one of the first asymmetric key algorithms used for exchanging keys quickly and securely. Simply put, the Diffie-Hellman algorithm is helpful when you need to find a way for all systems to receive a private key. The image below shows the principle of Diffie-Hellman.
As you can see, Diffie-Hellman works when you need to set up a secure communication channel to be further used by systems to exchange a private key, which, in turn, is then used to establish a symmetric method of encryption between systems.
Using NaCl to create cryptographic tools
NaCl is a software library that provides the core operations needed to build higher-level cryptographic tools. NaCl is characterized by the following features:
Data-dependent branches.
The history of cybercrime knows a number of successful timing attacks that have captured secret keys from the CPU instruction pointer and branch predictor, as these components are not tailored to keeping data secret. NaCl avoids the transmission of private information to both of these CPU components.
Data-dependent array indices.
The CPU’s cache and translation lookaside buffer (TLB) are not tailored to keep addresses private. With NaCl, you can prevent any data leakage caused by cache timing attacks by avoiding all flows of secret data to addresses applied in load and store instructions. The pattern of memory access is predictable, and there are no array lookups with indices based on private data.
No dynamic memory allocation or copyright restrictions.
NaCl is a public domain software library. Although more advanced programming languages like Python can’t be used in restricted environments, there is also the C-language version of NaCl. It’s designed for use in environments that cannot guarantee the availability of large amounts of heap storage but that nevertheless rely on cryptographic computations. In the C language, NaCl functions can’t call malloc or sbrk. They use little stack space, which we will eventually measure with separate benchmarks. This feature is available only with the C version, however.
How to ensure your data security?
As a security service provider, Yalantis makes the most of all the technologies and approaches we’ve mentioned to ensure the highest level of data security.
Let’s see how we solve the problem of encryption and decryption for group chats.
Key generation and exchange
To ensure secure message encryption and establish encrypted connections, we generate all required keys once a chat is created. To achieve additional network security, we generate keys for each individual chat, meaning that keys generated for chat A are useless for chat B.
As discussed earlier, we use the Diffie-Hellman algorithm as a secure way of exchanging keys between parties.
We also apply Curve25519, an elliptic curve providing 128 bits of security that’s specially designed to be used with the Diffie-Hellman elliptic curve. We’ve used Curve25519, XSalsa20, and Poly1305 as encryption, decryption, and message verification algorithms. Android, iOS, and Golang, which we use for backend development, all have native libraries for these three algorithms.
A holistic approach to ensuring data security
On the Healthfully project, one of our main objectives was to provide proper data security. Data security is especially relevant for the healthcare domain, given strict security requirements of laws like HIPAA (the Health Insurance Portability and Accountability Act) and heavy fines for leaking patients’ data.
We ensured HIPAA compliance and product security by:
- Making PII (personally identifiable information) and PHI (protected health information) visible only for users with permission to view it
- Setting session expiration times as well as controlling the number of devices logged in simultaneously
- Providing an encrypted communication layer (SSL)
- Allowing only SSL-based connections for data exchange between user and server
- Incorporating a strict password policy
Read more: How Can Python Help Your Organization Outperform Your Peers?
Concluding remarks
The best you can do to achieve maximum security and ensure your business protection is to apply cryptographic standards that are likely to be relevant for the next five to ten years. Closely following NIST guidelines helps Yalantis find the most relevant solutions that have already proven efficient. For example, Realm has its own cryptographic mechanisms that we apply to the apps we develop.
There are multiple effective ways of protecting, securing, and managing data including encryption, strong user authentication, backups, and erasure. All of them are worth independent articles. In this post, we’ve tried to distill the mandatory components of a cybersecurity barrier.
Note that you can always rely on data security experts to implement security measures specific to your business. After a massive 2016 data breach, Uber hired an outside firm to conduct an assessment of their data security solutions and then implement recommendations to adopt data security best practices. This step was aimed at establishing methods to safeguard user data stored on third-party platforms and to build strong password protection policies. In 2022, when data seems to become more vulnerable every day, involving data security experts is a good idea to protect your users and their data.
Apart from this, if you are interested to know more about List of Online Courses Available for Cyber Security then visit our Technology category.